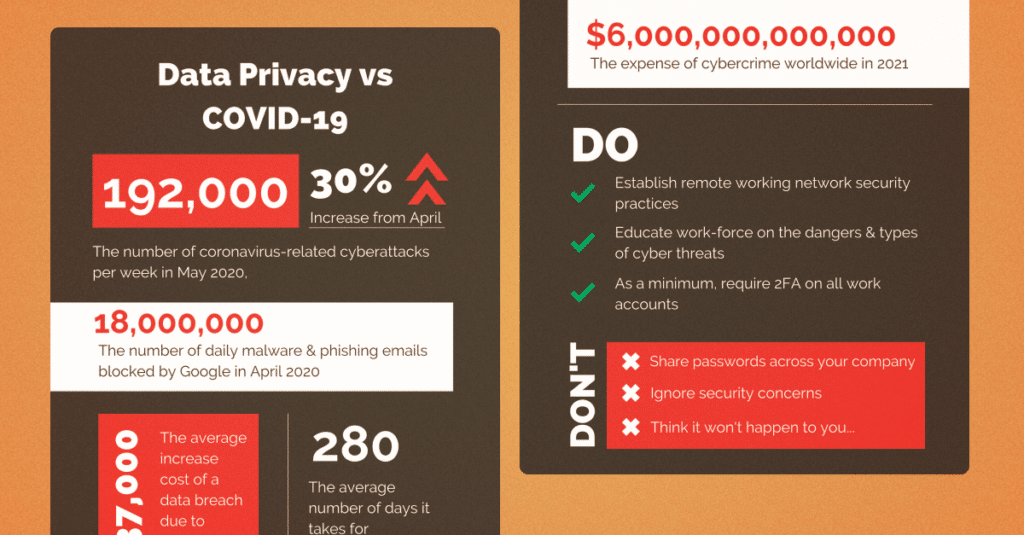
Data Privacy vs COVID-19.

In March 2020, as COVID-19 was beginning its attack on the world, news broke about a data breach at Virgin Media. Nearly a million customer details were accessed by ‘at least’ one person outside the company, after a marketing database was left open for 10 months. The Chief Executive decided not to notify customers because ‘we all have enough on our plate with coronavirus.’
The impact of COVID-19 has fundamentally changed how we work, with millions suddenly home-based and using their own computer equipment and, without the protection of corporate firewall and data security policies, a huge opportunity for online criminals to gain access to data and scam people quicker and more easily, has been created.
With such a big issue having been created, and the ever increasing pressure of keeping customer data protected, we decided to reach out to a few of our clients in the Cybersecurity space to discuss these issues to see what advice and insight they have that can help us all stay protected both professionally and personally.
Andy Smith is CMO at Laminar Security, a data security company that recently came out of stealth mode with a $32 million Series A investment.
Shimrit Tzur David is CSO at Secret Double Octopus, a world leader in passwordless, multi-factor authentication.
Q1: What are the top threats to businesses today that we all need to be aware of?
AS: Without a doubt, it has to be data breaches.
ST: The greatest threat is authentication. The attack surface is bigger than it’s ever been and we can see this with the popularity of ransomware attacks which, in most cases, starts with some broken credentials.
Q2: What are the biggest errors companies are making when it comes to data security and protection.
AS: Too many companies have a lack of visibility and monitoring when it comes to sensitive data that’s stored in the cloud.
ST: I think that most companies do not understand that the security of the whole organization depends on the “weakest” user/use case. An attacker only needs one user to choose a weak or guessable password, or click the wrong link in order to access the internal organization’s network.
Q3: Is this why 6 out of 10 companies suffered a ransomware attack in the last year, causing on average 6 days of downtime to affected businesses?
AS: It’s the lack of attention to the problem and lack of defense in depth, layers of security in place, such as a zero trust model.
ST: Yes. There are billions of leaked credentials and out of all of these, hackers just need to find one account to breach a system. Once they’re in, they’ll download the ransomware and you’re done.
Q4: So, what type of data is the most vulnerable and sought after?
AS: Sought after is payment card data, anything that’s personally identifiable and health records, vulnerable is “shadow data” that security is not aware of.
ST: The answer is clear on this one, simply credentials as that’s the first step for hackers.
Q5: What are the most common forms of cybercrime?
AS: Ransomware just outpaced phishing for #1 attack
ST: Phishing, dictionary attacks, guessing passwords, social engineering etc. Basically, anything that will give you those credentials.
Q6: What do you see as the biggest challenges facing the Cybersecurity industry over the next 5 years?
AS: Security practitioners need to change either attitude from defining themselves as gatekeepers and now thinking of themselves as business gate-openers with the proper guardrails.
ST: Remote working increases the attack surface as employees can access sensitive information via unsafe networks, they’ll sometimes be using their own personal devices which may not be secure enough and they’ll be doing so while the organisation is unable to control their own security practices.
Q7: It’s estimated that the global cybersecurity workforce will need to grow by a staggering 65% in order to defend the critical assets of organisations. What needs to happen in order to fill this massive shortfall?
AS: Automation with cloud-native security solutions would help with this.
ST: Cyber security is seen as an IT-based role, but the reality is that employees without a background in IT can transition into cybersecurity roles, especially with cyber-specific training more readily available now.
Q8: As a marketer, handling data is part of the job. What do we need to be aware of to keep our data safe?
AS: You need to establish continuous monitoring solutions to discover, prioritize and protect sensitive data in the cloud.
ST: In order to keep data safe, we need to ensure that both local data, and that which is kept at 3rd parties, is saved and managed securely. This includes access management, passwordless authentication, data in motion security etc. You’ll also need to ensure that your 3rd party vendor can match your own security standards.
Q9: On a personal level, what can we do to protect ourselves?
AS: Use a password manager and set up 2-factor authentication everywhere you can
ST: You need to focus on prevention and doing whatever you can to keep attackers away.
Q10: Are there any final comments you’d like to make?
AS: Security is about the data, not the infrastructure it sits on. Today we are system-centric security and world is evolving to data-centric security.
ST: Securing an organisation is not an easy task, it usually includes many steps and some 3rd party vendors. Make sure that each vendor you choose really target your need and don’t compromise on security of user experience; you can have both.
Now, bring a Brit and having worked in the pharmaceutical, Critical National Infrastructure and Defence industries, I know a thing or two about data protection and with the roll out of GDPR in 2018, I’ve sat on steering groups, created company policies and consulted on keeping marketing data safe.
For me, there are two or three really key comments Andy and Shimrit made that, as marketers and business owners, we really need to take notice of:
- 3rd Party Vendors. If you use an external 3rd
party to manage your email lists, or you have a CRM that an external vendor also has access to, you have to make sure that their security standards match yours. Without this, who knows what will really happen with your data. And, with only 69% of the world’s countries having formalised data protection legislation and the emergence of remote working, you really need to keep a close eye on your vendors and data processors. - Education We’ve all rolled our eyes at yet another boring corporate email from IT, yet as marketers, we have the power to take this information and turn it into something people will relate to and more importantly to engage with. So, if you’re an IT person thinking about sending another blanket email out, don’t. Engage your employee comms team, or your CMO and ask for their input first.
- 2FA. If you’re not already utilising the protection that 2FA offers, you’re doing something wrong, especially as more and more of us are working remotely and still have access to corporate shared drives and so on. Dial up the security, get 2FA mandatory for when your staff login to work platforms and keep your data secure.
The only thing missing in all of this is to think about access rights and global permissions within your business. Google makes is so easy to give access to anyone with a link to documents that sit within your Google Drive and Workspace. All your employees need to do is make a copy and then share with whoever they want. Now, think about this but through the eyes of a hacker who gained access to your employee via their stollen or weak credentials.
While annoying, this is actually something that Microsoft do really well as your IT team can set global security standards about downloading documents, sharing externally and a whole host of other security permissions. Yes, someone will always find a way around your policies if they are that determined to, but make sure you do what you can to limit the damage that a breach could do.
Extra bonus: Intrigued to know the cost of cybercrime in 2021 or find out how many malware emails Google blocked in April 2020? Click here to read our Data Privacy vs COVID-19 infographic.